Bartosz Kruszelnicki
Senior Technical Engineer | Senior Middleware & Integration Specialist
Experience
Senior Middleware & SRE Engineer — Instant Payments 2.0 @ Worldline
October 2018 – Present
Progressed from junior to senior within the Instant Payments 2.0 program,
managing dozens of environments and client integrations in a 24/7, high-availability payments ecosystem.
Core stack: RHEL (Linux), JBoss EAP, Tomcat, AMQ,
databases, load balancers, networking and security.
Key responsibilities & achievements
- Owned full lifecycle of enterprise JBoss & AMQ environments:
provisioning, configuration, version management across environments,
client onboarding and connectivity setup, security & certificate management.
- Deployed and maintained JBoss and Tomcat application servers,
handling application packaging, deployment pipelines and lifecycle management
across test, staging and production environments.
- Designed and built complete AMQ infrastructures ensuring reliable messaging
and integration for multiple business clients.
- Planned and implemented environment provisioning:
request & sizing of compute (CPU/memory), storage and network resources (VLANs, firewalls, load balancer rules)
to fit business and compliance requirements.
- Drove security hardening and compliance: TLS/cert management,
OS & middleware baselines, vulnerability remediation, audit readiness.
- Automation & IaC: Bash & Python tooling,
Ansible for configuration management, Terraform for cloud/platform resources.
- CI/CD: pipelines with Jenkins and XL Deploy
(artifact promotion, blue/green & rolling strategies).
For personal projects I prefer GitLab CI over Jenkins.
- Production operations (24/7): incident response, root cause analysis,
capacity/availability planning, Java performance tuning (GC, heap, threads).
- Developed ad-hoc Java applications to handle edge cases,
e.g. migration support or client-specific integration workarounds.
- Identity & integration: LDAP/SSO support (OpenLDAP/389-ds),
certificate lifecycle, compliance with security frameworks.
- Stakeholder leadership: SPOC for major clients, mentoring juniors,
leading interviews, running knowledge-sharing sessions.
CI/CD & Cloud Migration — Move2Cloud Initiative
2022 – Present (parallel to core Instant Payments 2.0 role)
As part of the Move2Cloud transformation program, I supported the migration of legacy applications
towards containerized and cloud-ready environments. My work focused on CI/CD modernization,
OpenShift administration, and cloud enablement for new and existing projects.
Key responsibilities & achievements
- Implemented and maintained CI/CD pipelines using
GitLab CI, Jenkins, and XL Deploy
to support automated builds, deployments, and artifact promotion across multiple environments.
- Worked as OpenShift administrator for several cloud-based projects,
handling namespace provisioning, resource quotas, RBAC, image streams, and route configurations.
- Refactored and containerized legacy applications to run on
OpenShift-based clusters — converting Java EE monoliths into container-ready services.
- Collaborated with development teams to define deployment pipelines
and environment strategies optimized for resilience, rollback, and compliance.
- Built automation scripts in Bash and Python
to streamline configuration drift detection and deployment consistency across environments.
- Gained hands-on experience with Google Cloud Platform (GCP) and
Google Kubernetes Engine (GKE), supporting new client applications hosted in the cloud.
- Contributed to Move2Cloud knowledge-sharing sessions,
promoting containerization standards and DevOps best practices across teams.
- -
LINUX eg Redhat 7+, Ubuntu (cert RHCSA)
LDAP systems: OpenLDAP & 389-ds
Previous Experience
Throughout my high school years (2011 - 2014) at MAK-NET [Internet Service Provider], I served as a technical support specialist. My role encompassed a range of responsibilities, from configuring network devices to installing antennas and links, addressing clients' device issues, and troubleshooting connection hiccups. This multifaceted role immersed me in the intricacies of UNIX-based network infrastructure, particularly with the MIKROTIK variation, enhancing my expertise in this domain.
minor experience
between elementary school and starting university, I operated my own IT service venture, specializing in tasks like OS reinstalls doing some kind of SPA for devices. that time I initially engaged with LINUX/UNIX systems.
Education
Wrocław University of Science and Technology (2014 - 2018)
Bachelor of Science in Systems Engineering with specialization in control systems
Systems Engineering with
specialization of control systems
was great mixture of mentioned
technologies in folowing areas:
IT:
including programming, DB, app design, OS knowledge
Automation & Robotics:
Mainly in programming area, great example might be creating
soft for lifts that control engine.
Al:
machine learning algorithms for example face
recognition, classifying texts
High School nr 1 in Kępno (2010 - 2014)
Specialization in Information Technology: Operating Systems and Computer Networks
Certificates & Trainings
- EX280 (Red Hat Certified Specialist in OpenShift Administration)
- GOOGLE CLOUD - Associate Cloud Engineer Certification
- RHCSA (Red Hat Certified System Administrator)
- JBOSS, APACHE, TOMCAT [one-week workshop]
About Me
My journey with ATOS started with a student internship. After getting an offer to join full-time and being part of the Instant Payments 2.0 project, I found a great fit for my passion for IT. I'm into tech and economics, so I spend a lot of my free time reading and learning new stuff. Oh, and I love hanging out with my two awesome parrots!
Contact Information
Email: bartosz.kruszelnicki1@gmail.com
Phone: +48 537-565-469
Home Lab Projects
Home Workstation: Virtualized Network Infrastructure
As a personal project on my home workstation, I developed a fully virtualized network infrastructure that serves as a multi-functional environment for various IT services. Here’s a breakdown of the key elements:
- File Server for Local Network: Set up a dedicated file server for seamless local file sharing across the network.
- Web Servers with Auto-Renewing SSL Certificates: Hosted several websites accessible over the internet, with SSL certificates that automatically renew on a weekly check using Let's Encrypt. All services are available over HTTPS.
- Fedora and Ubuntu Virtual Machines (VMs): Managed over six VMs running either Fedora or Ubuntu. These machines are integrated with LDAP, ensuring unified user management across the entire environment.
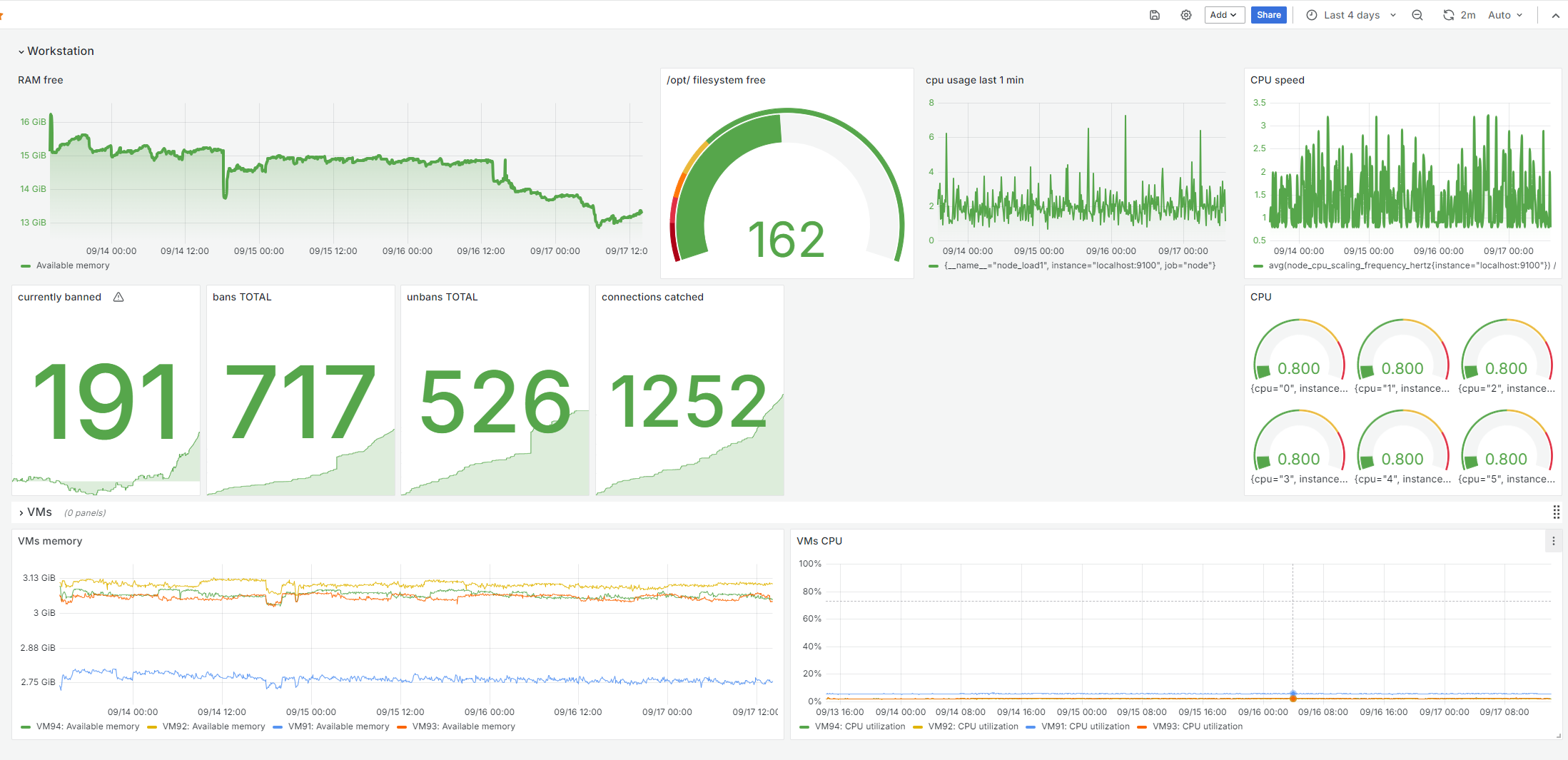
- Monitoring with Prometheus, Zabbix, and Grafana: Each VM and the workstation itself are continuously monitored using Prometheus and Zabbix, with Grafana providing real-time dashboards for system metrics such as CPU usage, memory, filesystem status, and CPU clock speed. Additional custom metrics include:
- The number of banned IP addresses (via Fail2Ban).
- Total IP bans, unbanned IPs, and blocked connections.
- LDAP Authentication Across Components: All critical components, including Zabbix, Grafana, Jenkins, and Kubernetes, are secured with centralized LDAP-based authentication, ensuring a consistent user experience.
- Jenkins CI/CD with Kubernetes: Configured Jenkins to build and deploy application images into the Kubernetes clusters running on the VMs. Jenkins itself, along with Kubernetes services, is secured via LDAP credentials.
- Kubernetes Cluster Hosting Websites: The Kubernetes cluster manages and hosts these websites and several others, leveraging a proxy and ingress for efficient traffic routing and load balancing between the hosted services.
- Fail2Ban Security Layer: To enhance security, the workstation is open to the internet and secured with Fail2Ban, which automatically bans IP addresses after two failed login attempts, with a ban duration of 48 hours.
- Secure Communication: All communications between services (HTTPS, LDAPS) are encrypted to ensure the confidentiality and integrity of data.
This project showcases my ability to build and manage a complex virtualized infrastructure with strong security, monitoring, and automated workflows, using technologies such as Kubernetes, Jenkins, Prometheus, Grafana, Zabbix, and LDAP.
Wyrażam zgodę na przetwarzanie moich danych osobowych zawartych na tej stronie
na potrzeby bieżącego oraz przyszłych procesów rekrutacyjnych, zgodnie z
Rozporządzeniem Parlamentu Europejskiego i Rady (UE) 2016/679 z dnia
27 kwietnia 2016 r. (RODO).
I hereby give consent for my personal data included on this website and in any submitted documents
to be processed for the purpose of current and future recruitment processes, in accordance with
Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 (GDPR).


